PenDoc: Penetration Testing Documentation & Collaboration Platform
Transform your penetration testing workflow with PenDoc—the comprehensive platform designed to streamline documentation, accelerate reporting, and enhance collaboration between security teams and stakeholders. From initial reconnaissance through final delivery and remediation verification, PenDoc keeps all findings, evidence, and client communications in one secure, accessible location.
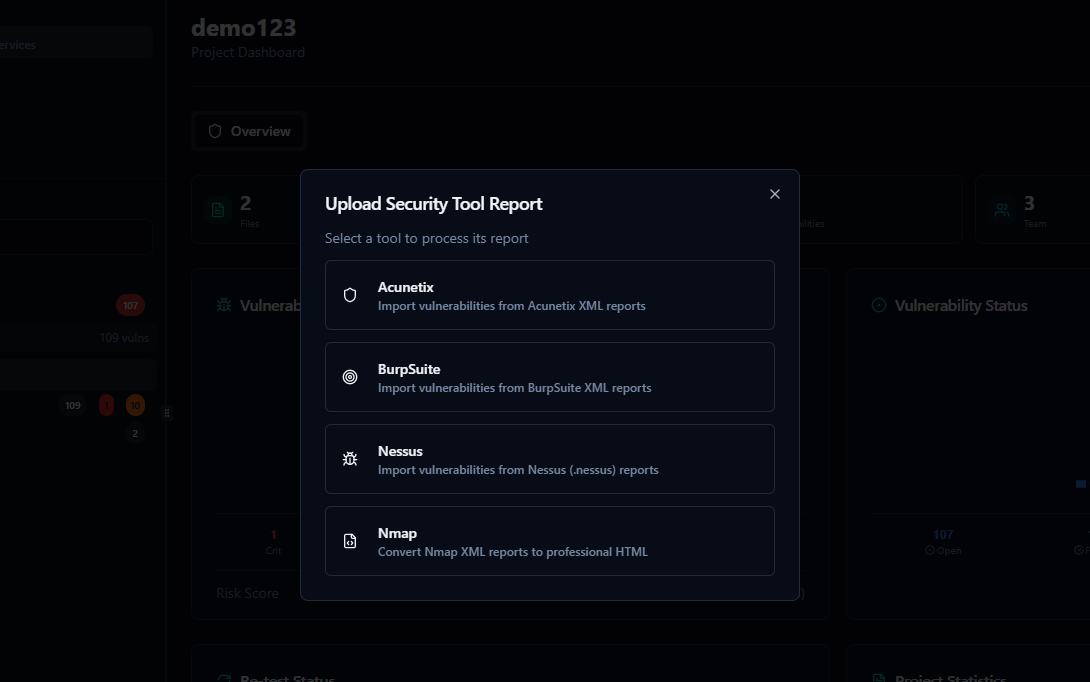
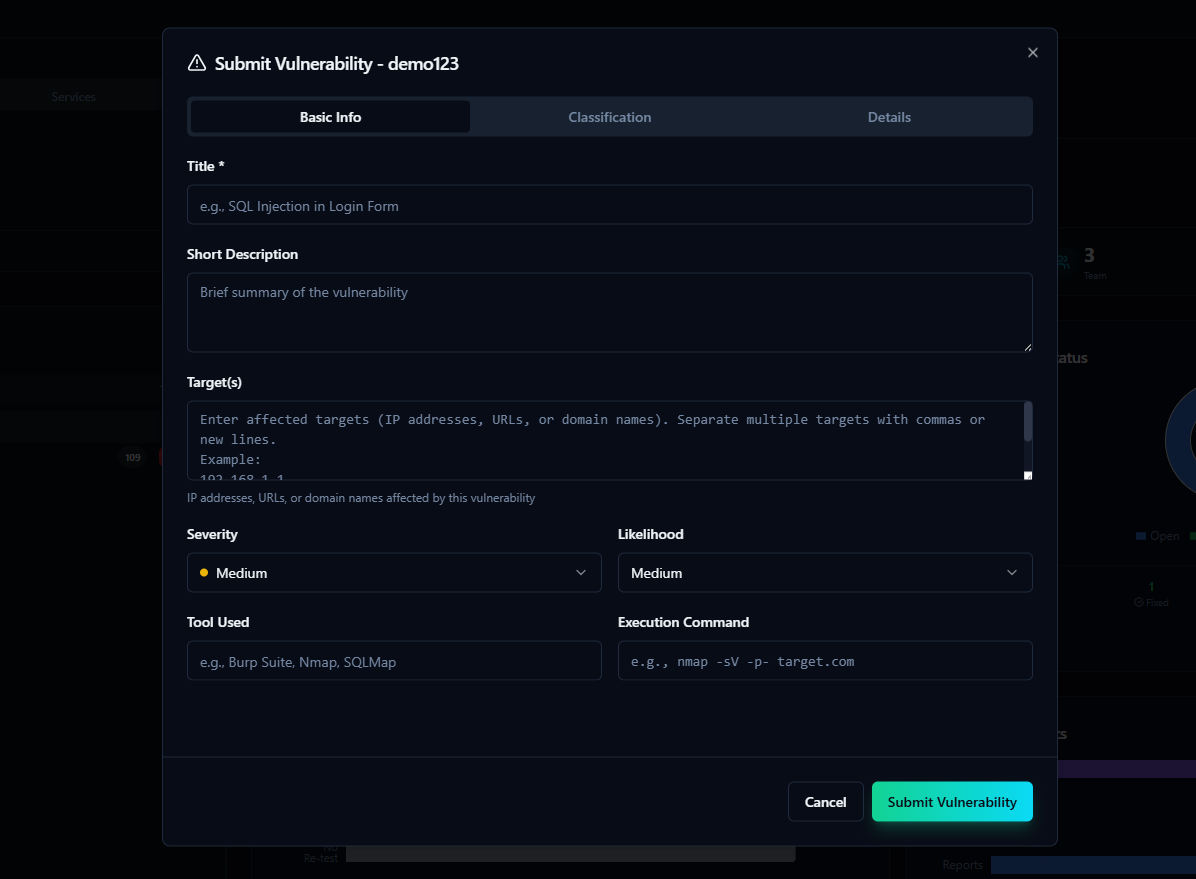
Centralized Evidence Repository
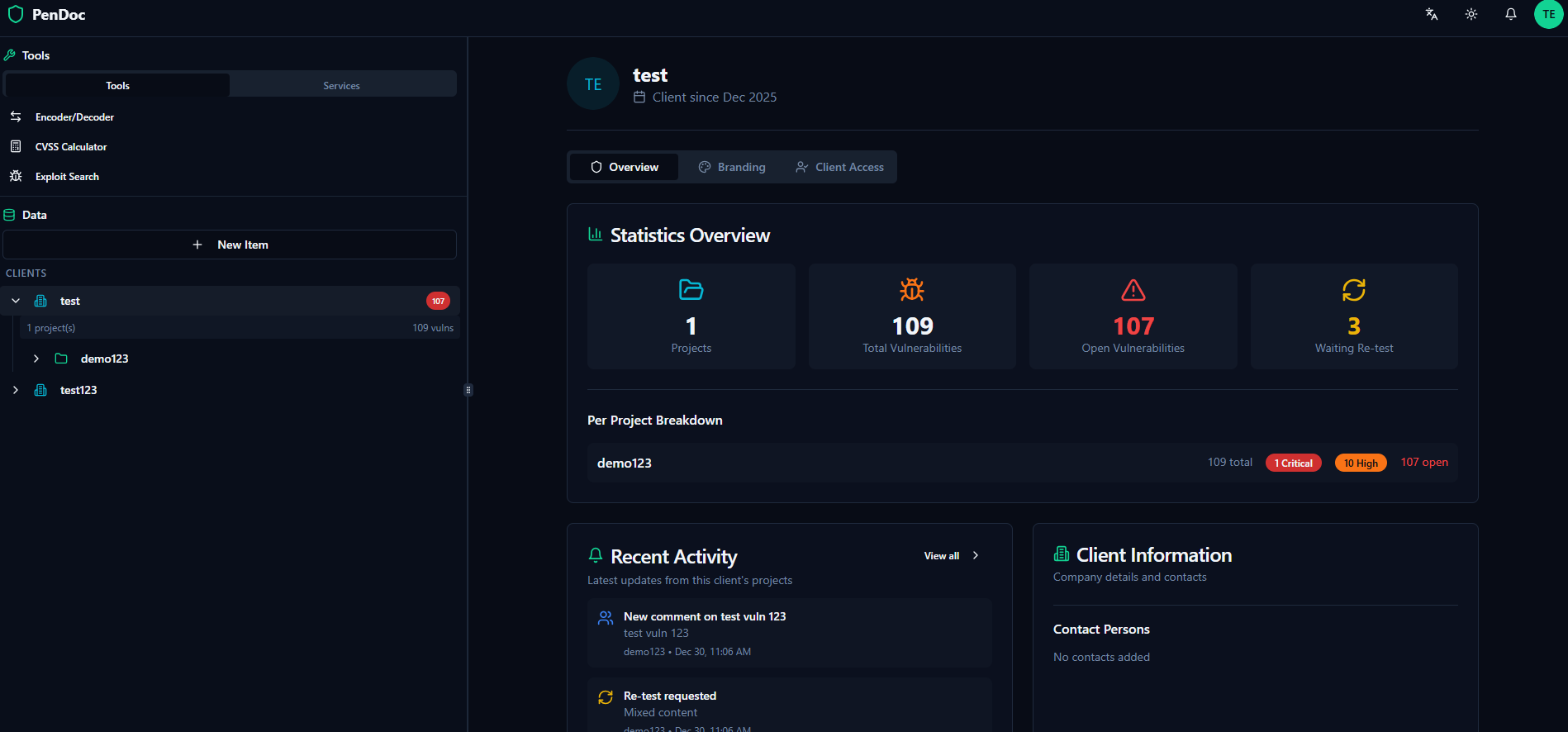
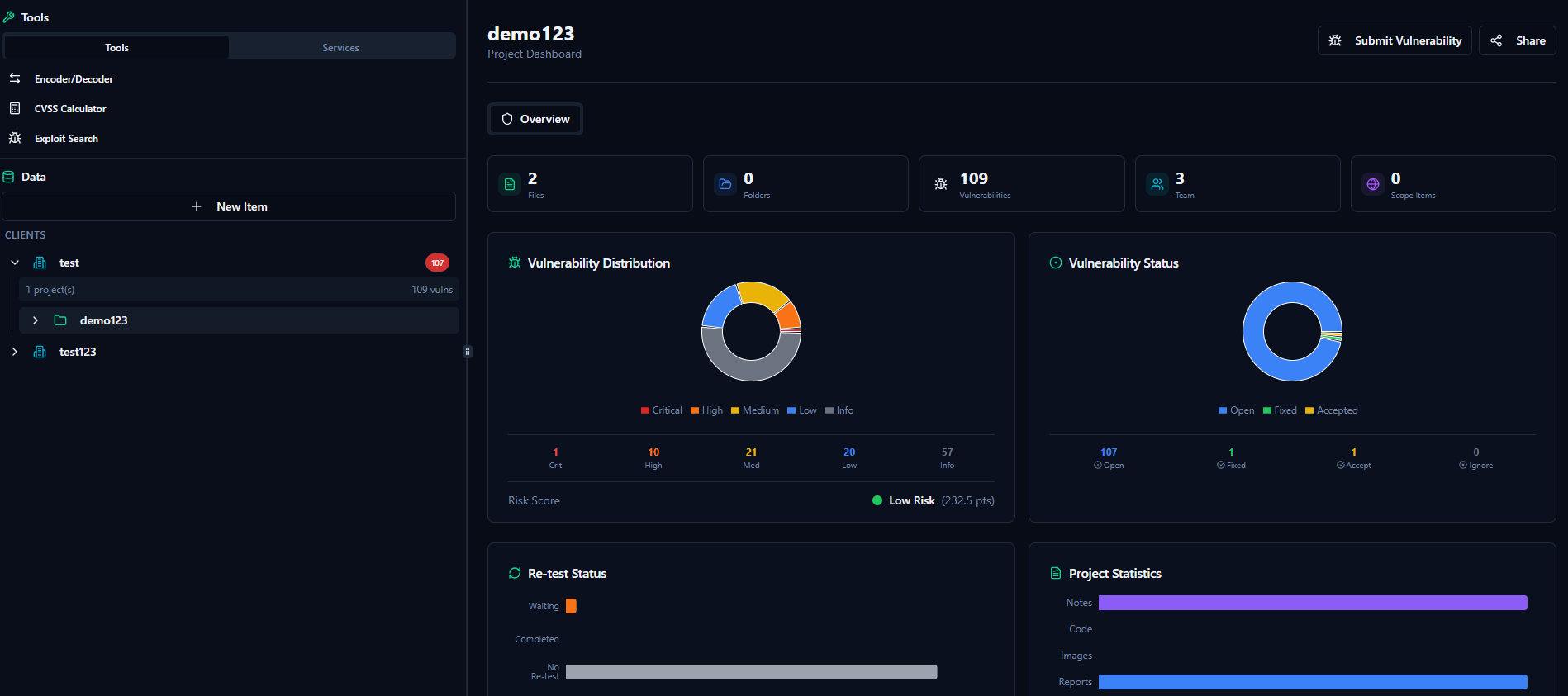
Securely organize and manage all findings, screenshots, proof-of-concepts, and supporting documentation in a searchable vault with full audit trails
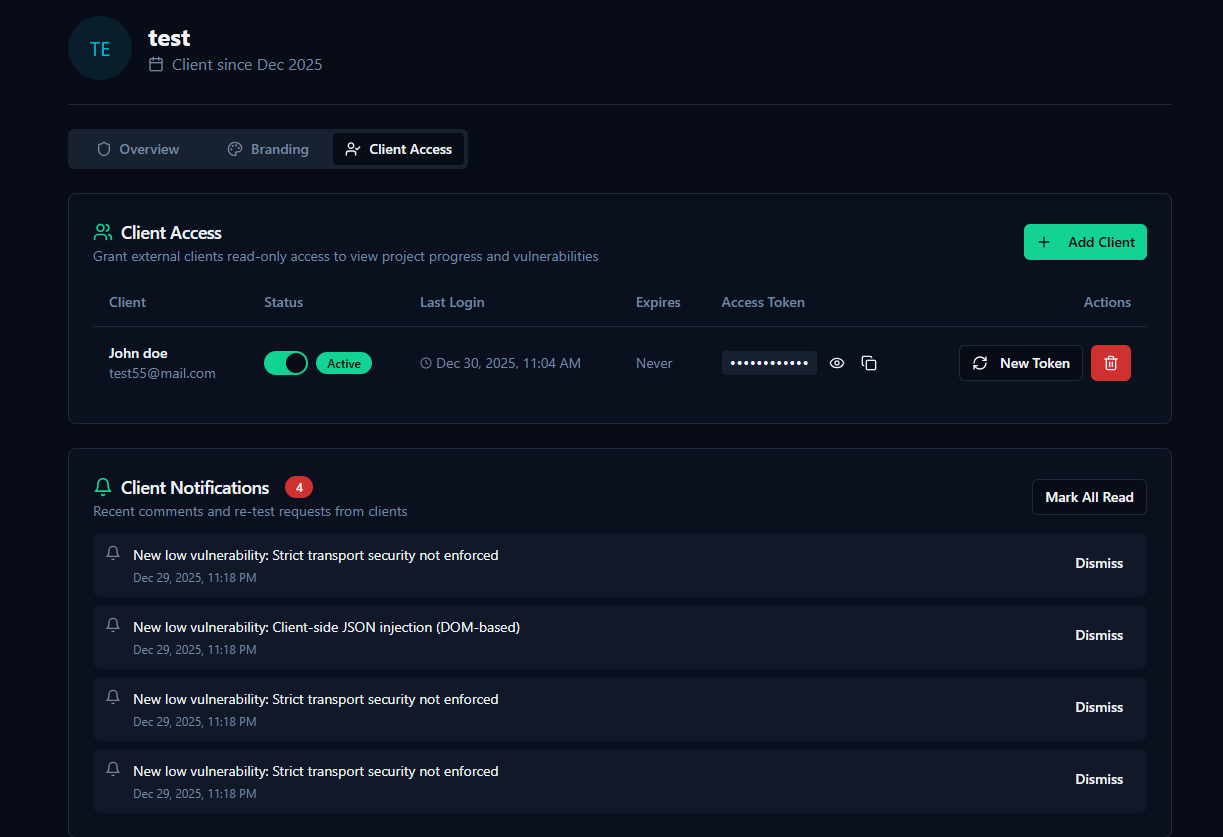
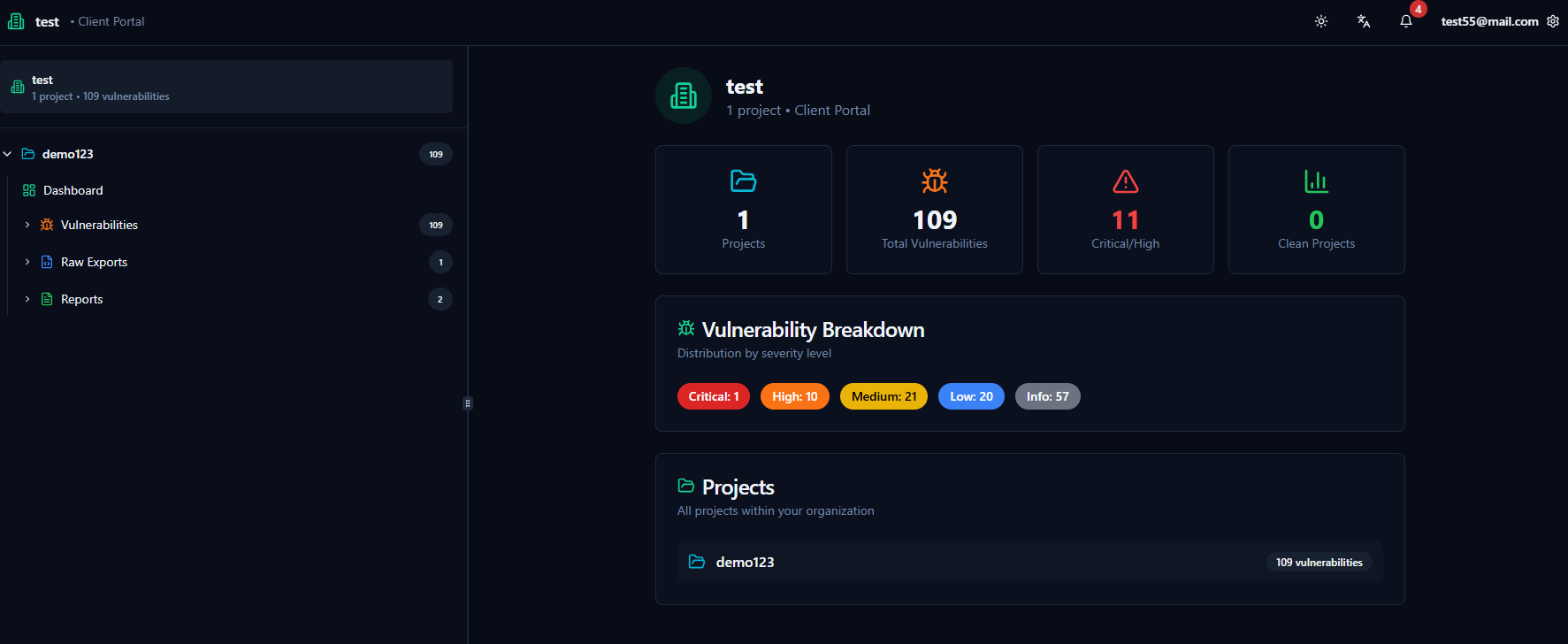
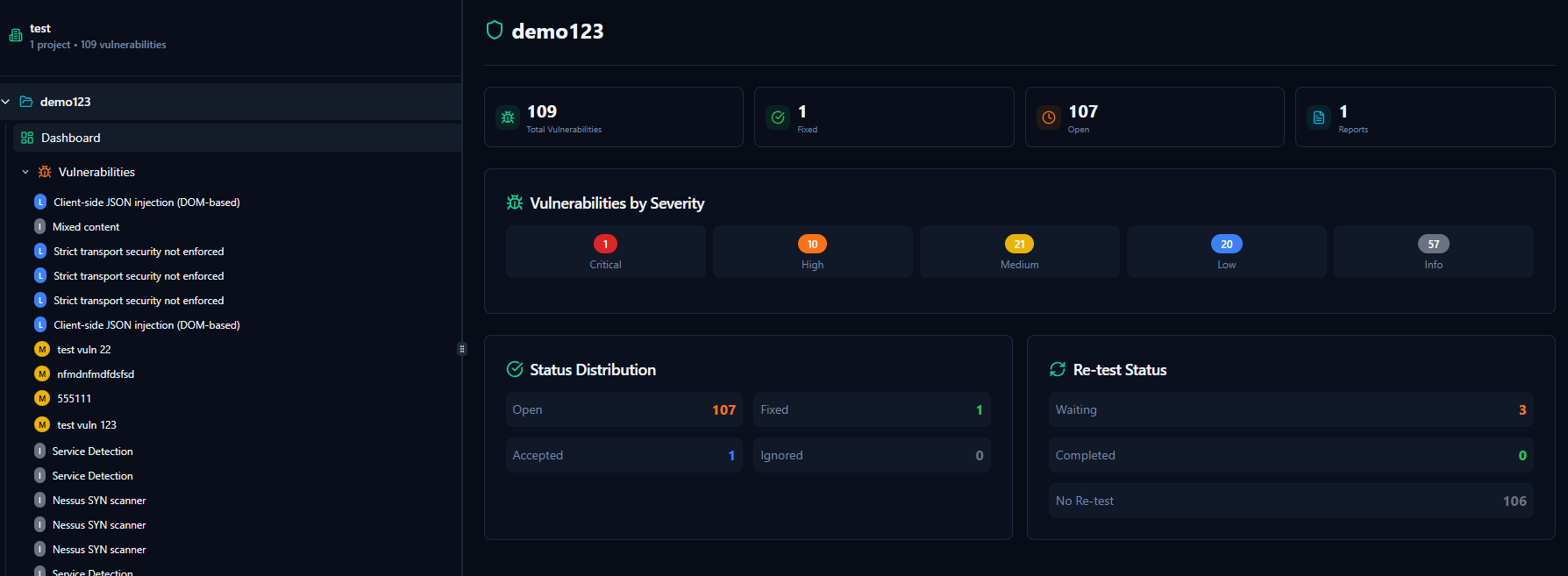
Client Portal & Transparency
Provide clients direct, real-time access to their vulnerabilities, remediation progress, executive summaries, and final reports without exposing sensitive test data
Automated Report Generation
Generate professional, branded reports for executives, developers, and compliance teams in minutes using intelligent templates
Real-Time Collaboration
Comment on findings, discuss remediation strategies, track status changes, and maintain complete communication history
Re-testing Workflow
Systematically track fix verification, schedule re-tests, document closure confirmation, and maintain remediation timelines
Encrypted Secure Messaging
Enable direct communication between pentesting teams and developers with end-to-end encryption and notification tracking
Pentest.Systems AI Assistant: Intelligent Penetration Testing Agent
Revolutionize your security testing workflow with our AI-powered penetration testing agent. Combining advanced vulnerability scanning, intelligent research execution, automated documentation, and expert-quality report generation, our AI Assistant accelerates engagements while maintaining human expertise and oversight at every stage.
Dual-Mode Architecture
Chat mode for real-time expert consultancy and quick research, Agentic mode for autonomous execution of complex penetration testing workflows
Automated Security Research
Execute reconnaissance, scanning, and security analysis autonomously, covering web applications, APIs, networks, and cloud infrastructure
PenDoc Integration
Automatically populate findings into PenDoc, maintaining documentation standards and enabling immediate client visibility
Enterprise Tool Integration
Connect with Shodan, Censys, VirusTotal, and custom databases for enriched intelligence gathering and validation
Notifications & Automation
Telegram and Slack integration for real-time alerts, scheduled campaigns, proxy support, and complex multi-step task chains
Custom Instructions & LLM
Tailor behavior with context-aware instructions, custom prompts, and support for multiple language models
PenDoc Scanner: Centralized Vulnerability Scanning Platform
Everything you need to discover, track, and remediate security vulnerabilities. Aggregate results from multiple security scanners, correlate findings, validate vulnerabilities, and generate comprehensive reports in one unified platform.
Multi-Scanner Integration
Integrate with Nessus, Acunetix, ZAP, Nmap, Nikto, Nuclei, and more to centralize your security data.
Instant & Scheduled Scans
Run immediate scans or schedule them for optimal timing to ensure continuous security monitoring.
Target Management
Create and organize targets into groups for efficient scanning operations and asset management.
Vulnerability Validation
Validate findings, mark false positives, and track remediation progress to focus on real threats.
Comprehensive Reports
Generate detailed reports in XML and HTML formats with full customization for different stakeholders.
Correlated Results
Aggregate and correlate results from all integrated security tools to get a unified view of your security posture.